Configuration ¶
User guide ¶
Pre-requisites ¶
You'll need an email to create and register your AWS Organization Management Account. For this purpose we recommend to avoid using a personal email account. Instead, whenever possible, it should ideally be associated, with a distribution list email such as a GSuite Group to ensure the proper admins member's team (DevOps | SecOps | Cloud Engineering Team) to manage its notifications avoiding a single point of contact (constraint).
Email setup example ¶
GSuite Group Email address: aws@domain.com (to which admins / owners belong), and then using the + we generate
the aliases automatically implicitly when running Terraform's Leverage code.
aws+security@binbash.com.araws+shared@binbash.com.araws+network@binbash.com.araws+apps-devstg@binbash.com.araws+apps-prd@binbash.com.ar
Reference Code as example
#
# Project Prd: services and resources related to production are placed and
# maintained here.
#
resource "aws_organizations_account" "apps_prd" {
name = "apps-prd"
email = "aws+apps-prd@domain.ar"
parent_id = aws_organizations_organizational_unit.apps_prd.id
}
Reference AWS Organization init workflow ¶
Steps for initial AWS Organization setup
-
Create a brand new AWS Account, intended to be our AWS Organization Management (root) Account
- Name:
project_name-management, eg:leverage-management - MFA: Enable MFA for your root user
- Billing: review billing setup as pre-requisite to deploy the AWS Org.
At your Management account billing setup
check
- Activate IAM User and Role Access to Billing Information
- If needed Update Alternate Contacts
- Name:
-
Via AWS Web Console: in
project_name-managementpreviously created account (eg, name:leverage-management, email:aws@binbash.com.ar) create themgmt-org-adminIAM user with Admin privileges (attach theAdministratorAccessIAM managed policy and enable Web Console and programmatic access), which will be use for the initial AWS Org bootstrapping.NOTE: After it’s 1st execution only nominated Org admin users will persist in the
project-managementaccount.
-
Via AWS Web Console: in
project-managementaccount createmgmt-org-adminIAM user AWS ACCESS KEYSNOTE: This could be created all in one in the previous step (Nº 2).
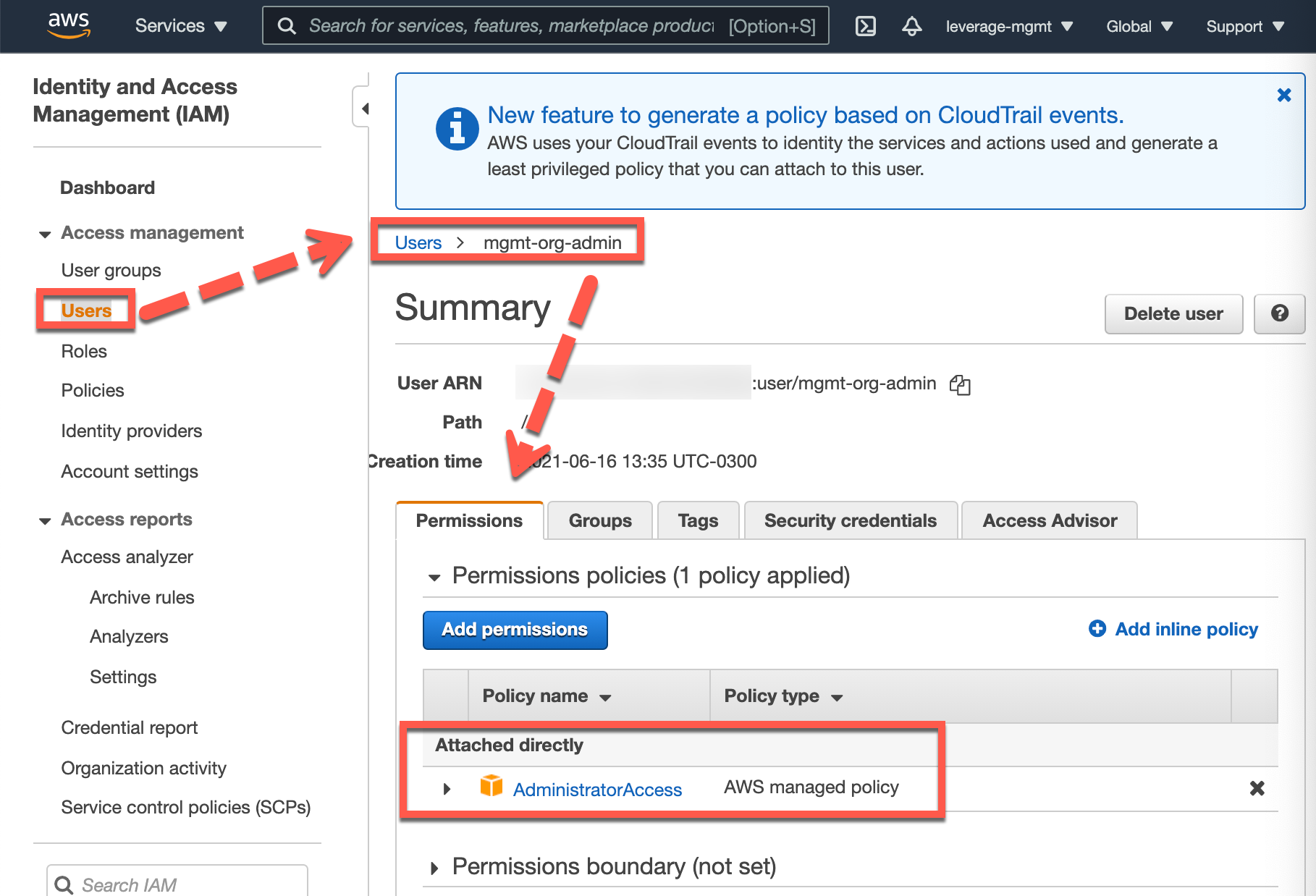
Figure: AWS Web Console screenshot. (Source: binbash, "AWs Organization management account init IAM admin user", accessed June 16th 2021). 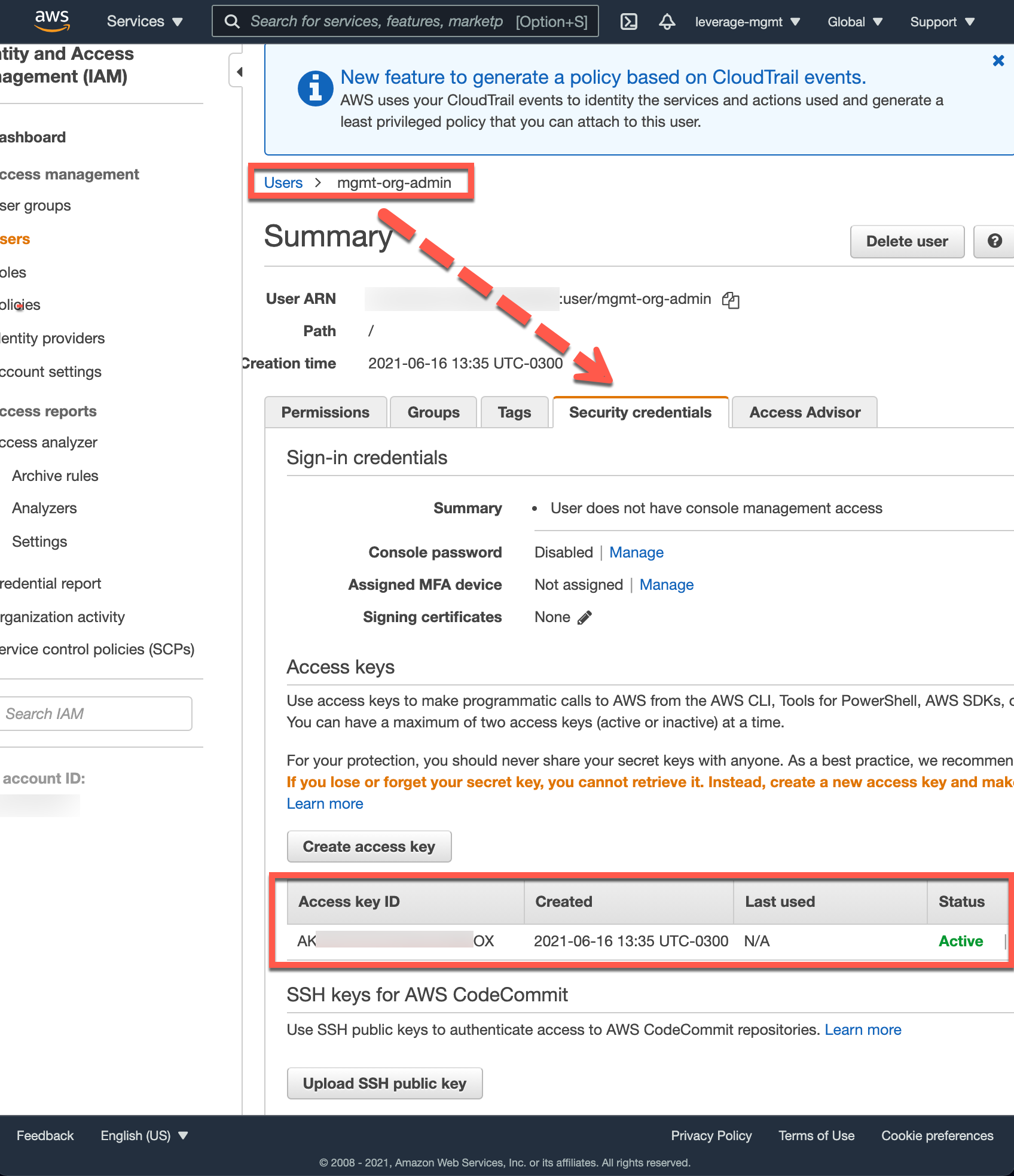
Figure: AWS Web Console screenshot. (Source: binbash, "AWs Organization management account init IAM admin user", accessed June 16th 2021). -
Set your IAM credentials in the machine your're going to exec the
Leverage CLI(remember this are themgmt-org-admintemporary user credentials shown in the screenshot immediately above). -
Set up your Leverage reference architecture configs in order to work with your new account and `org-mgmt-admin IAM user
-
Setup and create the terraform remote state for the new AWS Org Management account
- terraform remote state config
- terraform remote state workflow
- terraform remote state ref code
You'll 1st get a local state and then you'll need to move your tf state to s3; validate it and finally delete local state files
-
The AWS Organization from the Reference Architecture /le-tf-infra-aws/root/global/organizations will be orchestrated using the
Leverage CLIfollowing the standard workflow.the Management account has to be imported into de the code.
-
Verify your Management account email address in order to invite existing (legacy) AWS accounts to join your organization.
Organization setup post-steps ¶
AWS Organization setup post-steps
-
Following the doc orchestrate vía the
Leverage CLIworkflow the Mgmt Account IAM layer (base-identities) with the admin IAM Users (consider this/these users will have admin privileges over the entire AWS Org assuming theOrganizationAccountAccessRole) -> le-tf-infra-aws/root/global/base-identitiesThe IAM role:
OrganizationAccessAccountRole=> does not exist in the initial Management (root) account, this will be created by the code in this layer.
-
Mgmt account admin user permanent credentials set up => setup in your workstation the AWS credentials) for the
OrganizationAccountAccessRoleIAM role (project_short-root-oaar, eg:bb-root-oaar). Then validate within each initial mgmt account layer that the profilebb-root-oaaris correctly configured at the below presented config files, as well as any other necessary setup. -
Setup (code and config files) and Orchestrate the
/security/global/base-identitieslayer viaLeverage CLIon your security account for consolidated and centralized User Mgmt and access to the AWS Org. -
Pending to document the debug mode for the mfa script
